X-FORT Security.

Proper data protection not only protects enterprise information assets, but also utilizes and protects clients’ confidential information. According to The Identity Theft Resource Center, enterprise information leakage has become a serious problem in recent years. It is therefore urgent to control the confidential information without leak in order to protect the intellectual property and sensitive information. X-FORT is a total security Data Loss Prevention (DLP) that offers the best protection and assists in information security policy implementations.
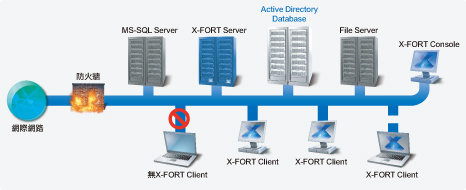
Architecture.
Functions of X-FORT:
● Prevention of Leakage through Computer Peripherals:
Control built-in storage devices such as USB Flash Disk, Mobile Disk, and memory cards as well as file output devices such as CD burner, printer, infrared rays, Bluetooth, etc. The hard disk theft protection mechanism prevents copying of hard disk contents through CD turn-on or hard disk connection. Also provide various read/write modes such as prohibited use, read, power-on-the fly encryption, and supervisor review for information safety and flexible use.
● Prevention of Internet Leakage:
Strictly monitor Network Neighborhood, e-mail, IM software, P2P software, FTP, Web upload when sending files. Also completely monitor internet 3G/3.5G internet card, wireless card, and dial-up internet service for total control over channel information outflow.
● Full-range PC Manager:
It includes full-range PC management functions such as software control, remote control, file distribution, PC asset management, integrated Windows Update or Hotfix of WSUS and provide comprehensive analysis reports for total PC control.
● Comprehensive System Structure:
Set up backup data and output records for audit use. It also features the client-server structure of auto backup and load balance to provide interregional large-scale enterprises with Multiple-server Management Console such as synchronized authorization among servers and encrypted file roaming.
● System self-Protection mechanism:
prevent destruction and removal by malicious users. It can be set up at the client's end without affecting users' PC access.
● Prevention of Leakage through Computer Peripherals:
Control built-in storage devices such as USB Flash Disk, Mobile Disk, and memory cards as well as file output devices such as CD burner, printer, infrared rays, Bluetooth, etc. The hard disk theft protection mechanism prevents copying of hard disk contents through CD turn-on or hard disk connection. Also provide various read/write modes such as prohibited use, read, power-on-the fly encryption, and supervisor review for information safety and flexible use.
● Prevention of Internet Leakage:
Strictly monitor Network Neighborhood, e-mail, IM software, P2P software, FTP, Web upload when sending files. Also completely monitor internet 3G/3.5G internet card, wireless card, and dial-up internet service for total control over channel information outflow.
● Full-range PC Manager:
It includes full-range PC management functions such as software control, remote control, file distribution, PC asset management, integrated Windows Update or Hotfix of WSUS and provide comprehensive analysis reports for total PC control.
● Comprehensive System Structure:
Set up backup data and output records for audit use. It also features the client-server structure of auto backup and load balance to provide interregional large-scale enterprises with Multiple-server Management Console such as synchronized authorization among servers and encrypted file roaming.
● System self-Protection mechanism:
prevent destruction and removal by malicious users. It can be set up at the client's end without affecting users' PC access.